Black Duck (by Synopsys) is a Software Composition Analysis (SCA) tool that scans application dependencies for:
Open-source vulnerabilities
✔ License compliance risks
✔ Code quality issues
✔ Security policy violations
It integrates into CI/CD pipelines to detect and mitigate risks before deployment.
Software Composition Analysis (SCA) is the process of scanning and analyzing open-source and third-party dependencies in an application.
Identifies outdated, vulnerable, or non-compliant dependencies
SCA tools analyze package managers and source code to identify components and match them with known vulnerabilities.
Process Flow:
1️ Scan Dependencies – Identify all open-source and third-party components.
2️ Check Vulnerabilities – Compare against databases like NVD (National Vulnerability Database), OSS Index, or Black Duck Security Advisories.
3️ Analyze Licenses – Ensure compliance with software licenses (e.g., Apache, MIT, GPL).
4️ Generate Reports – Provide insights on security risks, policy violations, and outdated packages.
Real-Life Use Cases
📌 Example 1: Preventing Vulnerabilities in Banking Apps
A banking company uses Black Duck to scan third-party libraries for security vulnerabilities before deploying financial applications. This prevents the risk of exploitable vulnerabilities in critical services.
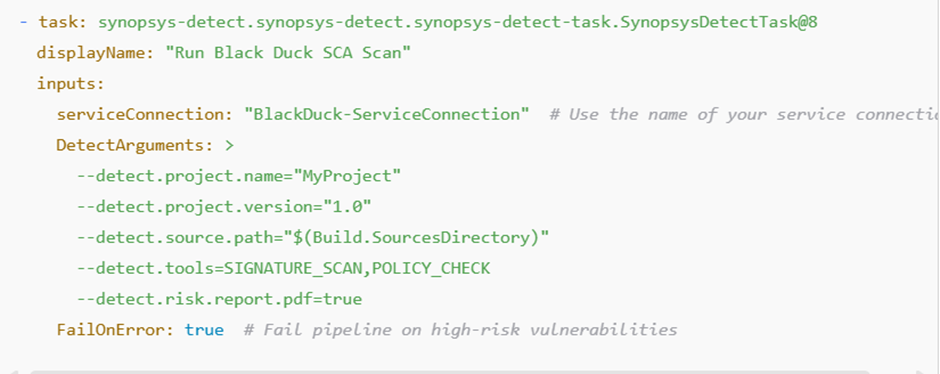
How to use in pipeline
We need to first setup project name and BitID and share to blackduck team so they can approve particular id for upload data and files.
Bitid for managing whole project under one id.
Use Synopsys Detect Task task for automates the Black Duck SCA scan so no need to install CLI.
How to Configure a Service Connection for Black Duck?
1️ Go to Azure DevOps → Project Settings → Service Connections
2️ Click New Service Connection → Select Black Duck (or use “Generic”)
3️ Enter Black Duck URL (https://your-blackduck-instance.com)
4️ Enter API Token (from Black Duck)
5️ Save and Name it (e.g., “BlackDuck-ServiceConnection”)
What type of issue it catch
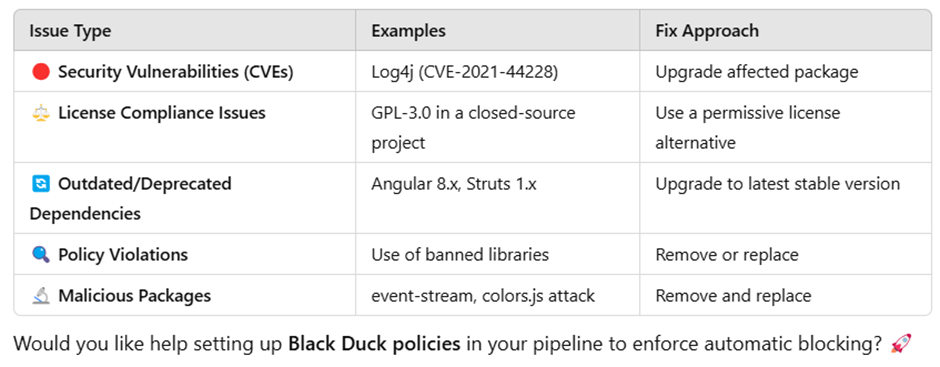

How does Black Duck detect vulnerabilities in third-party libraries?
✔ Scans package managers like npm, Maven, pip, Gradle, etc.
✔ Uses signature-based analysis to identify components.
✔ Compares against National Vulnerability Database (NVD) and other sources.
✔ Flags outdated or unpatched versions.
How can you configure Black Duck to fail a pipeline if critical vulnerabilities are found?
Use the –detect.policy.check.fail.on.severities=CRITICAL,HIGH flag in the pipeline.
What are best practices for using Black Duck in DevSecOps?
✔ Automate scans in every pipeline (shift-left security)
✔ Fail builds on high-severity vulnerabilities
✔ Enforce license policies to prevent legal issues
✔ Monitor new CVEs for existing dependencies
✔ Generate SBOMs for compliance and audits
✔ Use webhook alerts for real-time vulnerability updates


